DLP framework and roadmap for strengthening cyber security analytics framework
Data loss prevention
Enterprise endpoints are points of egress for all kind of data including business and personnel. It is, therefore, critical to monitor endpoints for user behaviour patterns and prevent insider threats causing data exfiltration or accidental data leakage or exposure. Cloud, mobile and BYOD adds complexity to the data theft problem.
In hybrid environments, millions of user activity data points collected over thousands of endpoints and devices by disparate security monitoring tools do not reveal the sequence of events in a comprehensive way. Tracing the data loss to a specific employee and device creates a huge and complex issue to solve for SOC analysts.
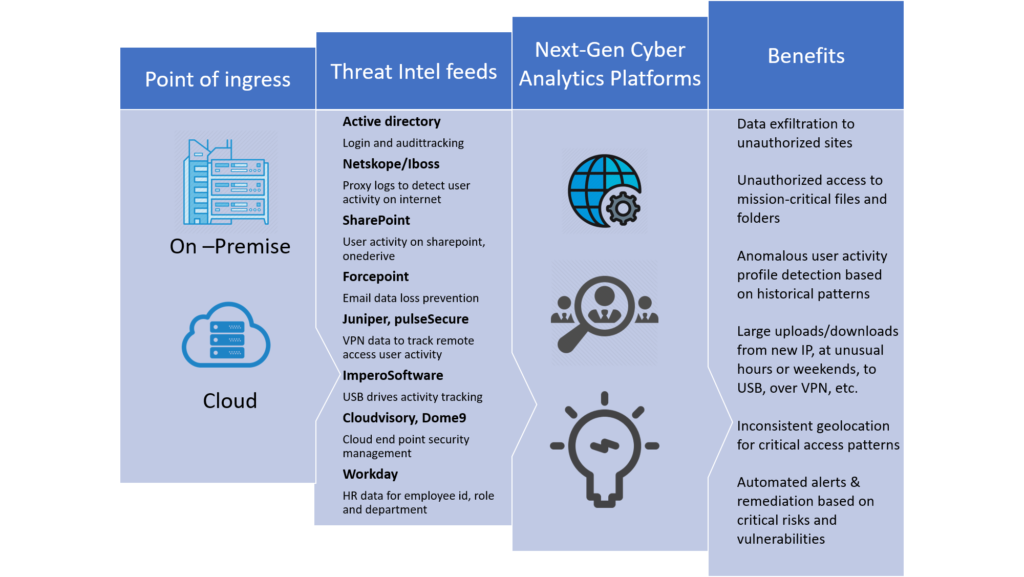
For example, a cyber analytics platform can combine internet activity data from Web monitoring tools such as Netskope, Zscaler or Iboss with user activity data from Microsoft SharePoint, OneDrive/Google drive and other cloud collaboration tools and add intelligence from endpoint user activity monitoring security agents. Such agents include Forcepoint, which tracks universal serial bus (USB) security, and other technology player, which detects unauthorized access to file servers, email systems and Microsoft Active Directory.
Organizations can further enrich this data with VPN and geolocation data to check remote access by users and human resources data to validate users’ authorized role and department. This helps to create a comprehensive user behaviour analysis and validate operational sequences of an employee in real-time.
By incorporating advanced analytics such as machine learning and AI, it is now possible to identify and isolate anomalous user behaviour when compared with past behavioural patterns and current role privileges. This approach of user and entity behaviour analytics (UEBA) helps organizations quickly identify and classify high-risk activities and user accounts. Automated security policies can be integrated to notify or suspend high-risk user accounts or change vulnerable security access controls for the user.
A next Gen Approach for strengthening the SIEM
In recent years, the topic of security analytics has become closely interrelated with SIEM products, with most vendors in this space launching products built around native AI and ML analytics capabilities, such as the Microsoft- Sentinel, Fireeye-Helix AI platform. Concurrently, security analytics players are launching into the SIEM market in the form of XDR or MDR.
The platform had to be developed from scratch. In fact, some have been inching away from ground-up custom analytics platforms to commercial off-the-shelf (COTS) solutions. Some of the good example are Fireeye, Cylance AI and Microsoft- Sentinel.
By far, the greatest failure is not clearly defining the security control use cases for analytics. Entire companies have been founded to address this need with commercial threat intelligence services such as Fireeye-Mandiant or Cisco- Talos which generates up-to-date blacklists to refine the event data in the platform. organisations also struggle to not just detect but also respond to the overwhelming number of security incidents.
Recruiting data science expertise to mine the data lake is difficult – this skillset is one of the rarest and most expensive in the industry. This can be easily avoided if an organization focuses on addressing the security events rather than analysing and detecting them, which can easily be handed off to a more specialized partner or vendor.
Finally, fully managed security services, which provide organizations with business outcome-driven, orchestrated security operations based on multi-tenant analytics platforms, such as MSSP offerings by some of the top security vendors.
Going Forward
Organizations need to assess their cyber risk from an organizational, cultural, structural and talent perspective and evolve their security practices and policies to solve the cybersecurity challenges.
By adopting an AI-driven security automation framework, organizations can align their cybersecurity maturity with digital maturity. Such a platform must be able to analyse and correlate threat patterns on massive volumes of multisource data, which introduces opportunities for advanced cybersecurity without business disruption.
Security automation can help mitigate resource skill gaps and cybersecurity knowledge issues. This can expedite threat hunting, insight generation and remediation. Moreover, organizations must cross-train SOC analysts and upskill team members to face digital threats and elevate security best practices and awareness among the broader employee base of an organisation.
The current threat environment requires a more proactive and adaptive approach that incorporates continuous monitoring and real-time assessments. Guidelines recommended by industry-standard risk assessment frameworks like the National Institute of Standards and Technology (NIST) Cybersecurity Framework. Other way to protect the company’s assets with the framework of Zero Trust framework adoption basis the dynamics of company’s environment and use cases.
Cybersecurity is an evolving and moving objective. Organizations must continuously adapt their cybersecurity technology landscape and multiple models to improve their preparedness and build confidence in their ability to proactively face, detect and block potential cyber threats. Organisation need to put focus and not bypass their cloud environment which normally isolated thinking that protecting the cloud environment is the sole responsibility of a Cloud service provider- CSP.
Digital and cloud enabled businesses requires a hacker like thinking and digital cybersecurity covering all aspect of an IT area that makes the best use of advanced analytics and intelligent automation. This helps in achieving digital objectives at a pace and scale that outsmarts and defeat threat vectors.









