How to solve cybersecurity challenges with AI and ML (Part-1)
Using an AI-powered analytics platform, organizations can shift from a reactive approach to security breaches, to proactively identifying increasingly sophisticated threat vectors and quickly resolving exploitable vulnerabilities.
Executive Summary
In a recent report from Identity Theft Resource Center (ITRC), the number of breached customer records containing personally identifiable information (PII) skyrocketed to 34 million records leaked. Significant 2020 breaches include those experienced by Cognizant, Twitter and few BFSI customers in India including Facebook, Under Armour and Marriott International in last few years. The study also points out that the resulting customer churn from loss of brand reputation and consumer trust was a leading contributor to the increased indirect costs of a data breach.
Threat vectors are only multiplying as more enterprises move to digital approaches for doing business and embrace a wide array of internet-connected devices, cloud and social media. Even as organizations implement emerging technologies into their core businesses to safeguard their information crown jewels, malicious agents are also evolving, thereby increasing the nature of deceptive and automated cyber-attacks.
Given the unprecedented levels of data and analysis involved in a hyper-converged networked world, we believe traditional defence mechanisms and siloed security tools are unequipped to address the ever-evolving cyber threat landscape. Cybersecurity now requires advanced analytics that keep pace with the speed and scale of digital business. This means IT organizations must leverage big data, cloud and with artificial intelligence (AI)-powered analytics to provide predictive insights and threat protection.
The current cyber threat landscape
A robust cybersecurity defence strategy needs to account for latest, sophisticated threat vectors, as well as the more sophisticated attacks possible through the advent of cloud enablement, IoT initiatives, big data analytics, social media, mobile computing, cryptocurrencies, etc.
The current threat landscape is characterized by following three trends:
1) No body is fully protected to Cyber-attack- All industries are prone (Matter of luck): No industry is untouched and all industry domains like BFSI, Healthcare, Manufacturing, e-retail can be attacked and breached.
- The cost of Equifax’s data breach in 2017, for example, was about $300 million. Indirect costs resulting from organizational resources spent notifying victims and investigating the incident, as well as the loss of goodwill and customer churn, also have substantial financial consequences. Moreover, regulatory changes such as the European Union’s Global Data Protection Regulation (GDPR will enforce strict penalties for any privacy lapse.
- Hacking is one of the most popular choice of attackers. Unauthorized Access was the second most common method of breach.
Four major cybersecurity challenges and how to handle those:
- Cybersecurity initiatives are failing to keep up with accelerating digital threats. Roughly 84% of respondents in a recent study feel companies are insufficiently prepared for the vulnerabilities caused by IoT initiatives and 49% of CIOs in a Gartner study say their enterprises have already changed their business models or are in the process of changing them.
With connected technologies and IoT, companies must shift from managing security for thousands of network endpoints, to millions of connected devices. With the adoption of container technologies, IoT devices, mobile devices and cloud infrastructures, many organizations’ security tools and processes lack visibility into the new resulting threat vectors.
Action item: IT and Businesses need to broaden the data points collected for real-time integration and employ security automation to centralize management and enable rapid, flexible deployment. Security should not be the cosmetic add on but need attention from top management under continuous review.
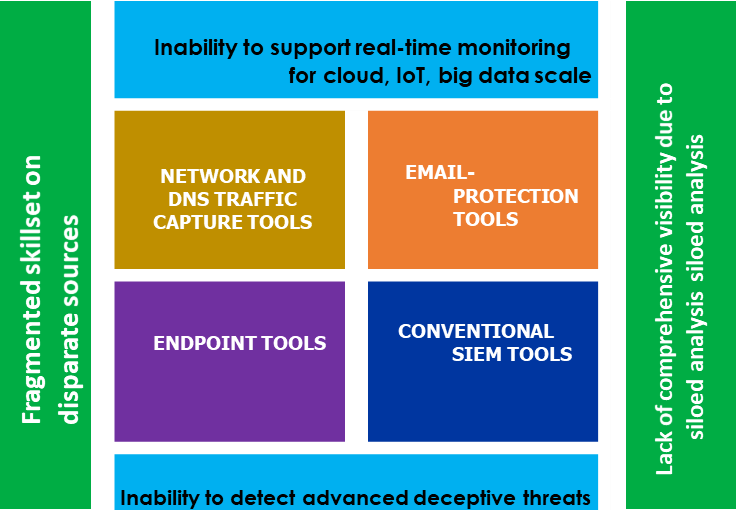
Limitations of traditional cybersecurity approaches
- Bots are annoying. While advanced analytics and AI are driving digital business change, malicious agents are reinventing attack algorithms, using AI to create new variants of old attack models. This adds to huge problems with traditional security tools that rely on human intervention and manual investigations and don’t always provide 360-degree cyber protection. The potential misuse of advanced analytics technologies can include automated hacking, email and social media phishing attacks.
Action item: Acknowledge the world of sophisticated threats and evolve from a reactive to a proactive strategy. Organizations need to employ advanced analytics powered by AI and machine learning to detect deception.
- Siloed data analysis that generates too much noise. Organizations typically use either traditional security information and event management (SIEM) solutions such as syslog servers and log managers, or they utilize multiple cybersecurity products that collect huge volumes of system and user activity events, independently. This results in disparate and disconnected systems that are not suited to today’s digital models and fail to present the complete picture of the IT health and risk posture at any given point in time. A conventional SIEM can only corelate correctly in ~9% of the alerts in time and in rest of the cases not at all effective.
The analysis of huge volumes of fragmented data results in a lack of comprehensive visibility, false positives and inefficiency. The mean time to identify (MTTI) for a data breach is anything around ~200 days. The failure to quickly detect and contain a data breach also has huge direct and indirect financial impacts.
Action item: Evolve from a piecemeal process of analysis. Organizations should adopt innovative thinking to intelligently integrate disparate data to radically increase insight generation and response.
- There’s a lack of cyber skills and capabilities in the emerging technology landscape. Given that the human factor is a significant cause of data breaches – there is clearly a critical need to improve awareness among the broader employee community. Conventional education and standard procedures are simply not enough to face the mounting challenges in the digital world, where attack models are outpacing acquired skills.
Security operations center (SOC) analysts with knowledge limited to a specific security tool will struggle to put together a holistic picture from multiple security tools. This will make it difficult to realize the comprehensive event-chaining behaviour and analysis of an incident or anomaly. A lack of skill and confidence in the cyber defence strategy can also hinder an organization’s IT modernization and digital growth plans.
Action item: Inform, educate and upskill SOC analysts and avoid internal fragmentation of cybersecurity skill and knowledge. Organizations need to overcome the lack of human-driven intelligence with analytics-driven intelligence.
As per my experience of a very long with multiple organisations of around ~20 years, organisations just treat cyber security as overhead and thought of it as a business barrier. Lot of IT leaders prioritize IT operations over IT security due to short term benefits over the cyber security controls around People, process and technology. Cyber Security controls and effectiveness needs an attention from the topmost of the organisation and should be under a continues review mechanism through multiple stakeholders specifically from independent CISO/CIO, CFO, CEO’s office and board of the companies.
To be Continued……









